Croll Cracks Twitter
Hacker Croll started by building a profile of his target company, in this case Twitter. Basically, he assembled a list of employees, their positions within the company, and their associated e-mail addresses. After the basic information was accumulated, Croll built a small profile for each employee with their birth date, names of pets, and so on.
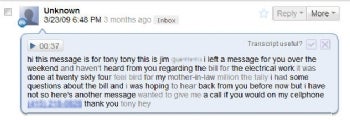
After Croll had created these profiles, he just went about knocking on doors until one fell down. That's exactly what happened when he did a password recovery process for a Twitter employee's personal Gmail account. Croll discovered that the secondary account attached to this person's Gmail was a Hotmail account. The problem was that Hotmail account had been deleted and recycled due to inactivity -- a longstanding policy on Hotmail. Now, all Hacker Croll had to do was reregister the Hotmail account for himself, go back and do the Gmail password recovery, and then Gmail sent the password reset information straight to the bad guy.
But it's not over yet. Gmail asked Hacker Croll to reset the password of the Twitter employee's personal e-mail account, which he did. But now the original user was locked out of their account, which would send up an obvious red flag. So all Croll did was search the Gmail account itself for passwords from the person's other active services. Then he entered a commonly used password he'd found, and waited to see if the person began using their account normally. Croll now had access to the Gmail account from behind the scenes, and was able to access information undetected. Making life even eaiser, the Twitter employee used the same password on her business and personal accounts, so the hacker now had access to both, and the rest was history.
Are You Vulnerable to the Same Crack?
The alarming thing about Croll's methods is they could happen to anyone. I checked my own Google account last week, and discovered I was open to the same security flaw the Twitter employee was. I had registered my Gmail account so long ago, that I'd forgotten all about my secondary e-mail address. Just like the Twitter employee, the secondary email attached to my Google Account was defunct and possibly open to re-registering by anyone. That has since been changed. I also did a search within my own email for passwords I've used, and I was amazed at how many results were returned. Do a search in your e-mail account using your most common passwords, and see what turns up. You might be surprised.
But there are a myriad of other ways a hacker could get your information. Have you ever received a Happy Birthday greeting on a public service like Twitter? Have you ever sent someone your phone number or any other information that way? What information is sitting on your social networking sites? Are your MySpace and Facebook accounts closed off, or can anyone view them who searches for you? Does your Facebook page have your birthdate, the past schools you've attended, your pet's name? Could your mother's maiden name -- a common security question -- be discovered through your social network account? What about the myriad of other services you use? If you think it's unlikely that someone could find this information, then try searching for yourself in the so-called "Deep Web" search engines like Pipl or Spokeo and see what comes up. You may find online accounts you'd completely forgotten about.
Webmail Security Similar
The other problem is that most of the major e-mail services use similar recovery methods to Google's. Hotmail is almost exactly the same as Gmail. Yahoo is even easier, since if you tell Yahoo you can't access your secondary e-mail account you can answer a secret question. Those security measures are what made it possible for a student to hack hack into Alaska Gov. Sarah Palin's Yahoo Mail account last year. In my tests of Yahoo Mail's recovery page, I got what seemed like an unlimited number of opportunities to guess my Yahoo Mail secret question. AOL Mail isn't much better, since you have a choice of entering your secondary e-mail (you have to know it or guess) or you can enter your exact birthdate plus your Zip code on file with AOL. The Zip code barrier makes it harder for someone to break in, but by no means impossible.
If you've discovered you're open to the same flaws that Twitter was, then consider this your wake-up call. You must regularly check the security settings on your various online accounts so that you remain in control of your security information since it's so easy to forget what you entered years ago. Pay special attention to secondary e-mail accounts connected to your primary e-mail address; consider giving a bogus answer (that only you remember) to security questions; and regularly change your passwords, either by your own invention or with a random password generator like GRC or Strong Password Generator. You could also get away from using just one or two passwords, and use password managers like Clipperz, KeePass or Yubico to remember your details instead. But perhaps most importantly, search for the most common passwords you use in your own webmail accounts and delete those messages. If the worst happens and your account is compromised, you'll be glad you did.